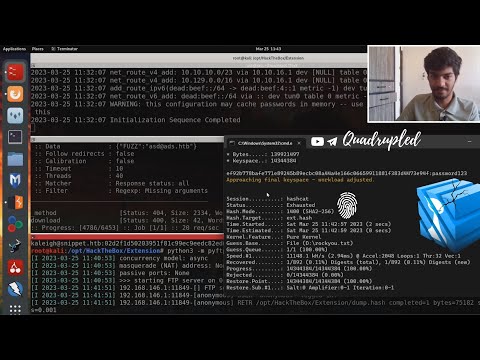
SHA256 is a commonly used cryptographic hash function that can create a fixed-length, unique representation of any input data. It’s often used to hash passwords before storing them in a database. While SHA256 is a secure hash function, it’s not immune to attacks, and that’s where Hashcat comes in.
We’ll start by explaining the basics of hash cracking, including the difference between hashing and encryption, and the types of attacks that can be used to crack hashes. We’ll then dive into Hashcat, exploring its features and how to use it to crack SHA256 hashes. Along the way, we’ll cover topics like choosing the right attack mode, selecting the best wordlists, and using GPUs to accelerate the cracking process.
Whether you’re a cybersecurity professional looking to improve your skills or just someone interested in learning more about password cracking, this tutorial will provide you with a comprehensive guide to using Hashcat to crack SHA256 hashes. So grab your favorite beverage, sit back, and get ready to break some passwords!
#hashcat
#passwordcracking
#SHA256
#cybersecurity
#infosec
#pentesting
#hacking
#cracking
#passwords
#hashcracking
#ethicalhacking
#cybercrime
#cyberattack
#encryption
#passwordsecurity
#cyberawareness
#cyberdefense
#cyberhygiene
#cyberthreat
#cyberprotection
#cybertraining
#cybereducation
#cybersecurityawareness
#cybersecuritytraining
#cybersecurityeducation
#informationsecurity
#networksecurity
#computersecurity
#passwordrecovery
#passwordmanager
#onlineprivacy
#onlinesecurity
#internetsecurity
#datalossprevention
#cybersecuritysolutions
#cybersecurityservices
#cybersecurityexperts
#cybersecurityconsulting
#cybersecuritytips
#cybersecuritynews
#cybersecuritytechnology
#cybersecurityinnovation
#cybersecurityresearch
#cybersecuritycommunity
#cybersecurityprofessional
#cybersecurityjob
#cybersecuritycareer
#cybersecurityskills
#cybersecuritycertification
#cybersecurityindustry
Take the opportunity to connect and share this video with your friends and family if you find it useful.

No Comments